Internet was undoubtedly one of the biggest inventions in the XX century. It is used for finding relevant information, staying in touch with friends and even shopping. However, due to its very large expansion, on average fewer people are aware of the dangers it poses. Can we protect ourselves? HTTPS is part of the answer.
Introduction
"Protocol" is a technical word used to describe a set of rules in order to communicate. The Internet is based on protocols. HTTP (Hypertext Transfer Protocol) is a protocol that forms the foundations of the World Wide Web a.k.a. websites. Usually, it can be seen in a browser what kind of protocol we are using:

In short, HTTP was created in 1991 when the internet was beginning to rapidly expand, therefore it is relatively simple because data is sent as nothing more than ASCII (American Standard Code for Information Interchange) code which can be very easily read as doesn’t involve any complicated mathematical formulae to be deciphered.
Everything would be great if the for the fact that data interception is not a myth although many would like to think so. In October 2003, the Open Project attempted to make an accurate visual representation of the internet. All lines on the picture on the left are connected in some way or another, some are quite a distance apart and the data has to go through many roots to reach the desired destination. A skilled hacker could attempt to intercept or “eavesdrop” for certain information. Therefore, a problem arises when there is a need to exchange some private or confidential information e.g. name or password to our email or bank account. However, HTTP is not the only protocol we can use.
Principles of Encryption
In 1977, Rivest, Shamir and Adleman published a paper called “A Method for Obtaining Digital Signatures and Public-Key Cryptosystems” introduced RSA - a basic encrypting algorithm. Although the principles of encryption had already known, the paper introduced mathematical way in which it could be achieved.
RSA algorithm is used as the base of another protocol called HTTPS (HTTP Secure). Using it ensures both confidentiality and security.
Confidentiality
In HTTPS, confidentiality is based on certificates which can be bought from special companies. Browsers verify whether they trust the company that realised the certificate; otherwise, you could call yourself “cs.your.ac.uk”, however, as browsers don’t trust you, they are going to alert the user. This process can be compared to acquiring a passport. Passport is issued by a government, which can usually be considered trustworthy “company”, therefore the document can be counted as a reliable identification.
Whenever one tries to call themselves “cs.york.ac.uk” with a certificate not acquired from a reliable company, the browser will warn us.
![]()
As opposed to:
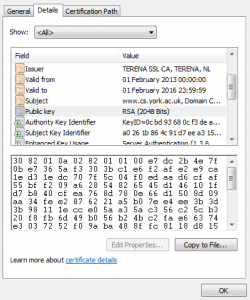
You can view the name of the company that issued the certificate in certificate details (see screenshot below).
Security
Security is really about how we exchange data and how well the data can be encoded. These are rather complicated mathematical functions and their complexity is measured by type the type of function and how many bits are used to encrypt a message. The more, the better. For example:
However, this is not all. RSA uses anti-symmetric key encryption. A key is a mathematical function for encrypting and decrypting text. Anti-symmetric key encryption uses a different key to encrypt the message and a different key to decrypt it. The key to encrypt the message is called the public key and the one used for decrypting is called private. The public key is available to anyone as anyone can encode the message.
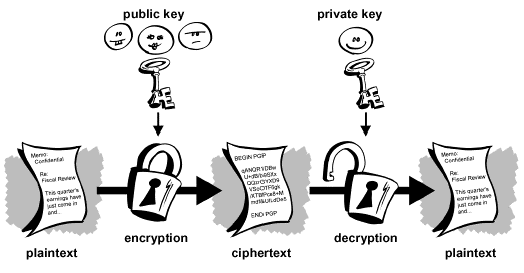
A sheet of paper with confidential information locked in a chest is a very good analogy. If one wishes to encode some data, they ask for a chest (public key). You put the sheet into the chest and once the chest is locked, it cannot be opened by anyone who doesn’t have the key to open the chest (private key). Even the person who encoded the data, as you only have the key to lock it.
Therefore, whenever this appears: ![]() the data are still “secure” they just may not travel to the right person
the data are still “secure” they just may not travel to the right person
Conclusion
Some discoveries in the last century made it possible to communicate and exchange information more easily, however they also introduced new threats and dangers. This is why when logging on to Facebook or Online Bank, HTTPS protocol should always be used. It ensures that the data are encrypted and protected from interception.
